Fortunately there is a much better competitor, Bitwarden which we’ve used for almost five years now and which you should use too. The interface is better, the browser plugin is far more reliable. Bitwarden is the creation of a sole creator, Kyle Spearrin, who built Bitwarden from the ground up in a superhuman effort, including doing support for a couple of years while he built Bitwarden up. Now of course there is a larger team in place but Bitwarden is still very close to the technical founding team and is much better for it.
All of the good things we say about using a password manager like LastPass below apply to Bitwarden.
The big players in the Macintosh password software are LastPass and 1password/Dropbox. It’s their business to keep your passwords secure. On the other side, there is the NSA who definitely would like into your password stash. Just how secure is your password trove when you use LastPass or 1password?
Password Data in the Cloud: Can LastPass Be Secure?
Many Mac users wonder whether using an online service for password storage is safe, specifically LastPass. One poster brought up the example of how Adobe was recently hacked and millions of accounts were compromised. Sony suffered a similar episode last year. Apple’s developer program was compromised and shut down for three weeks. Scale and expertise of the company is no guarantee against hacking at this point: Adobe and Apple are among the largest and most profitable software developers in the world (it’s the software which sells Apple gear and not the hardware, but that’s a discussion for another day). If anyone should be able to protect his data online, it’s those two corporations.
But these episodes shouldn’t worry LastPass users. LastPass stores our data encrypted online and the data is only decrypted locally in your browser with your key, which LastPass does not have.
On the other hand, any data you have in LastPass is easily accessible by the NSA.

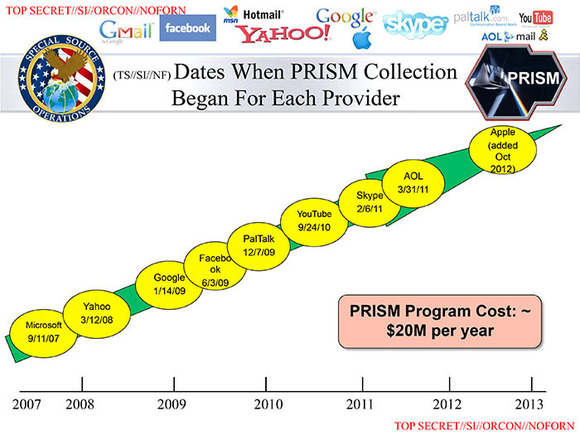
Prism compromised vendors by year: Dropbox was planned for 2013
As an American company, LastPass like Microsoft, Facebook, Google, Yahoo and Apple must provide a way to access their users accounts to the American security organs. What’s worse LastPass executives are not allowed to talk about their discussions or cooperation with the NSA under penalty of fine and/or jail.
So don’t expect any real revelations from LastPass CEO Joe Siegrist. He’s not really allowed to talk about it and he doesn’t want to go to jail.
LastPass’s Obligations as a US Corporation
LastPass is an American company. After the latest Snowden revelations one has to conclude that their data is vulnerable and the NSA at least has a backdoor into your account (or that the keys are vulnerable to brute force in a clean room environment). LastPass can claim reasonable doubt if they only pass on encrypted data to the NSA which the NSA has to crack themselves without the constraints of limited tries per minute.

Joe Siegrist has many good reasons not to want to go to jail
NSA Access to LastPass Data
What the NSA would want from LastPass ideally is a backdoor. Whether LastPass can do this and not have the backdoor revealed is an open question. There is a binary into which a backdoor could be safely inserted. But unlike Microsoft backdoors, LastPass is a one trick penalty. With security compromised with evidence of a deliberate backdoor, the company would be instantly worthless (at best only a non-American actor could pick it up with promises to clean up the service once it’s off-shore).
On the other hand, if the NSA had unlimited access to the data on LastPass servers, it would still be of enormous security value. Once that data is out of a protected environment, without query limits, the NSA can use traditional brute force hacking to break most LastPass vaults. For those where they fail, it’s not that difficult to get a keyboard logger or even a video camera or microphone into the environment of their target. What’s important is all that luscious data is in a single place.
As I mentioned, Joe Siegrist cannot talk about LastPass’s relationship with the NSA. But in 2011, there was a security breach to the LastPass servers, about which Siegrist could talk. Here’s what he had to say:
a potential attacker…could start going through and looking for people with weak master passwords without having to hit our servers. That’s really the threat that we’re concerned about….
You can combine the user’s e-mail, a guess on their master password, and the salt and do various rounds of one-way mathematics against it. When you do all of that, what you’re potentially left with is the ability to see from that data whether a guess on a master password is correct without having to hit our servers directly through the website.
The threat is that once somebody has that process down, they can start running it relatively quickly, checking thousands of possible passwords per second. If you made a strong master password, you are pretty much in the clear–it’s not really an attackable thing. But if you used a dictionary word, that is within the realm of someone cracking it in a reasonable time frame.
Siegrist has basically given away the NSA game plan for LastPass. Anyone whose vault they need access to comes under special scrutiny via offline hacking with the full set of data provided by LastPass.
Your run of the mill hacker would not have access to all the data on LastPass’s servers and thus represents a very limited threat (keyboard logging would be easier than cracking your LastPass database). But for those with the expertise and access to LastPass’s full data set, cracking any given vault is child’s play.
Thus spreading LastPass as far and wide as possible would be in the interests of the NSA. Much better to have that (relatively) secure data on an American server where they have unlimited access to all the bits and bobs in one place to be able to quickly crack the accounts they need than to have to hack into foreign servers just to get the raw materials to start cracking.
Free Service
Given the scale of LastPass’s free service (we are enterprise customers curiously enough), I’m somewhat apprehensive about their funding. How did they manage to survive the early growth without much revenue? A whisper into the ear of the right VC fund and funding can be made quickly available to a trojan horse.
1password (not) resisting the NSA

Jeff Shiner Canadian CEO AgileBits
If you want a fighting chance of keeping your passwords to yourself, you could try 1password from Canadian company Agile Solutions. For the moment, the Patriot Act and FISA does not directly apply to Canadians. On the other hand, I don’t think Canadians would do too well as tall poppies. While Canada suffers under the Stephen Harper Conservative regime, the US has almost unlimited reach in Canada. One could compare the relationship of Poland in the old Warsaw Pact to Russia.
Jeff Shiner CEO of 1password even claims 1password would rather shut down than comply with court orders to weaken their product:
The very real possibility that we would shut ourselves down (which would be public) rather than sabotage what we do and love should act as some deterrent to those who might wish to compel us to introduce a backdoor.
There’s no need for the NSA to compel 1password coders to provide backdoors. Why not?
Unfortunately the best way to sync 1password is with Dropbox, which is again a US corporation (although according to the Snowden revelations one of the last to fall under Goliath’s thumb). If you have your 1password data on Dropbox or iCloud (i.e. if you want to be able sync between physically remote computers which is the whole point of a service like this), you are no safer than when using LastPass.
At least LastPass has the benefit of being truly cross-platform (Linux too) and offering a free or very affordable service. We only pay about ten dollars per user per year for full enterprise LastPass as opposed to the many hundreds of dollars we would pay to 1password for just the licenses for 1password, without the fine enterprise account management LastPass offers.
Happy Thanksgiving America! The Patriot Act is a gift which just keeps giving.
Keeping your privacy and your passwords to yourself
If LastPassword and Joe Siegrist want to remain credible in the security field, they should move their servers and their operations out of the United States.
In the meantime if you want to keep your privacy, sell your Mac (or downgrade to 10.5.7 at least) or move to Linux. Do not use seLinux. Do your recreational browsing in a browser without cookies or flash. Reset the browser after each session. You can keep another browser for tracked logged in browsing (banking for instance). On those platforms, you can use keePass. Which is free.
Too hard? That’s the whole idea. For the moment, the guys in trenchcoats and fedoras have won. No worries. For a long time so did the Swiss guards (making sure Marie Antoinette enjoyed her cake) and the Tsarist secret police.

Alec Kinnear
Alec has been helping businesses succeed online since 2000. Alec is an SEM expert with a background in advertising, as a former Head of Television for Grey Moscow and Senior Television Producer for Bates, Saatchi and Saatchi Russia.







All encryption methods based on prime numbers can be easily hacked, because contrary to believe prime numbers can be calculated… Read this jmccanneyscience.com/calculateprimes.HTM.. There is a second method based on a hexagon… So all this Snowdon revelations are just part of a limited hangout operation for damage control
Of course can prime numbers can be calculated, otherwise where do you think the prime numbers used in “prime number based encryption” come from in the first place? To use an encryption scheme like RSA, you need two big prime numbers and where else would they come from if they weren’t calculated by your computer?
But the fact that prime numbers can be calculated doesn’t make prime number based encryption easy to hack. Encryption schemes like RSA base upon the fact, that it is very hard to convert a big number into its prime factors. If I ask you “What are the prime factors of 21”, you’d say “7 and 3, because 7 * 3 is 21”. Correct! How did you get that? What mathematical trick did you use? You didn’t use any trick, you just tried all possible numbers. That’s easy if the number is as small as 21, but what if I ask you for the prime factors of “48109189”? And that is still a very small prime number (RSA uses prime numbers that are as long as the text I just wrote above).
I can calculate thousand of large prime numbers a second on a powerful machine, no big deal, but I cannot magically split a very large number into its prime factors, other than trying out all possible “candidates”. And as there are far more than trillions of candidates. Testing all of them would take years, decades, actually centuries, even for the world fastest super computers (that are hundred thousand times faster than the fastest computer you can buy at a consumer store)
AES 256-bit encryption, which is what is used (and done locally) with LastPass has been “cracked” to the extent that it “only” takes a little over a trillion years to break with the best supercomputers. If the user in question doesn’t have an easily guessed password that the NSA or whomever else can guess at from other information, you’ll be perfectly fine.
Lastpass includes multifactor authentication… But even better; The encryption is deep, well salted, and the key is never sent over the internet – so the key is never present or available on the LastPass servers… The password information is always heavily encrypted with your secret key before even being sent to the servers – where it is then encrypted yet again.
The problem Broken is we have to take LastPass’s word on their security. It can’t be tested. On top of that LastPass is US resident so if they’ve been asked to compromise their network to the NSA, they are not allowed to tell us.
Good point Alec. But I’m not so convinced it could not be tested… I suppose if anyone could do it – it would be someone like Steve Gibson who is certainly no lightweight. Steve’s reviews, tests and analysis will often get down to the machine level as needed… I did find two review commentaries from him. One about LastPass, and another later about the NSA problem. Enjoy. grc.com/sn/sn-256.htm grc.com/sn/sn-421.htm
Is the author disputing LastPass’s claim that a strong password would enable the user to resist an attempted hack?
Hi David,
I don’t know how you are going to find out I answered as you entered a nonsense email, but yes I am. There’s no way for us to know what’s going on with LastPass and if they’ve got a back door, sold access to the NSA or been blackmailed (legally) to give that access.
Any onshore American technology company is obliged to give up all its secrets. That’s the cost of working in America or working with an American internet service provider.
Alec, When the encryption and decryption happens locally, I don’t think they should have access to your data unless they can crack your password. But yes with all backdoor, exploits and nsa snooping I don’t think there is any one way out to keep one safe.
Sachin Gopal /
“Do not use seLinux”.
Sounds interesting, could you please elaborate? Thx
Hi Bob,
seLinux was developed by the NSA (first release 2000). Yes, seLinux is open source but based on the NSA track record of work on Windows, Android and now Apple OS’s, I don’t think I’d like to use an OS which they developed themselves. I.e. inevitably there are backdoors. Very sophisticated ones but there nonetheless.
Further info about seLinux and back doors. Nils Torvalds (Linus’s father and a member of Finnish parliament) gave this official answer at a committee hearing:
I hope this helps.
You do not have to trust lastpass for most of the security. In the past I saw people that have checked lastpass using it’s transmissions and the plugin code and have seen it to be secure. It’s hard to find those checks because the internet is full of pages like this one asking if lastpass is safe. I personally use lastpass for everything. Before using lastpass I had the same password for every site and now I have a different password for each one that is random. I often max out web sites length or other requirements.
How can they share password if they are decrypted locally? (lastpass allow the sharing of password with friends)
Hi William,
The answer with LastPass is you can’t know. You have to take their word. But current American legislation does not allow LastPass to disclose if they have been spoken to and bent to cooperation with the NSA. The guy from Lavamail had to just shut down and couldn’t tell us much about why.
Lastpass is still operating so it’s pretty clear that they are “cooperating”. How cooperation on closed source software means anything else except sharing all your passwords with the US alphabet soup agencies is a mystery to me.
Alas, I’m less and less convinced that Lastpass is any real protection of privacy at all (however convenient it may be).
How about Encryptr and Crypton? These technologies have been developed via the makers of SpiderOak, who claim to have a dedication to zero-knowledge cloud storage and to data owners controlling their own privacy.
It strikes me as one of those cases.. If it sounds too good to be true, then it probably is. Still, the client is open source, and the server maintains zero knowledge, which strikes me as being one level better than LastPass. Perhaps the encrypted files are being shared wholesale with government agencies, but at least we can remain confident that there are no other back doors in place. No?
Would you use this solution over LastPass, even though it’s not as full-featured?
I keep all my data out of American control as much as possible because of the patriot act. Glad to see i’m not the only one worried about the gem of an act. I’ve got all stuff that matters on a private server which handles stuff like e-mail and cloud file storage that you’d normally use hotmail or gmail and google drive or dropbox for. Ofcourse this is still sub-optimal but at least there is no patriot act and keeping track of the my rights is a lot easier. There’s also no mining my files for ways to confront me with ads.
I’m fairly sure thats about as safe as you can get without unplugging yourself from the web, if you know how to configure an internet connected server in a secure way.
Your approach is absolutely right Kevin. There’s no guarantee that any company won’t become the next Dropbox (Condi Rice parachuted onto the board to make the boys give up their toys). Event DuckDuckGo or Startpage search could be co-opted in advance. With the tracking going on, it’s best to just turn off javascript in your main browser and clear all cookies. Safari is good for this with the developer tools turned off.
Final policy for what goes on the internet, anywhere. Think of your local celebrity paper (National Inquirer and People magazine in the states, DailyMail in UK, News in Austria, Plus7Dnej in Slovakia): would you be comfortable if the journalists there got ahold of the information and printed it on the first page.
Of course a bit more business information than you or I would like to see as front page news will have to go via email to remain viable than that but really keep it to a minimum. If it’s on the net, it’s been hacked or will be hacked. I wouldn’t keep too many years of IMAP online either. I’d suggest a single computer with local archives for email past six months. Anything particularly sensitive, I might take it down immediately (assuming it’s not on Gmail or Microsoft or Yahoo in the first place on one end or the other, in which case it’s already gone into the Matrix).
This is the truly weak point Kevin: only one partner needs to carry venereal disease for both to be infected. Even rooting Gmail out of Foliovision is difficult. Staff have personal accounts and we have to work with search tools and client Google+ accounts.
Checka/KGB surveillance in the Soviet Union was only a crude manual rehearsal for what is going on now in America and by extension the rest of the world. It’s laughable how our owners convinced us to call it “the free world” for the longest time. No prison has ever held so many inmates or been so difficult to escape.
Any recommendations for relatively user friendly password manager tools that are not US based and keep data elsewhere (where security laws are better?) Switzerland/ Norway etc….
Hi Jess,
If you are looking for a password sharing tool (rather than a private tool for one person), there’s only one usable application (there are others but they are out of date or have stone age interfaces – think Windows NT), the only one I know of is Passwork.me. The user is a decent chap and I’ve corresponded with him. He’s Russian, based in Russia. The server itself is in Switzerland. llya claims not to have access to your passwords (difficult to prove, one way or the other). He does not seem to be taking payola from the NSA. If he did, he’d be vulnerable to decades of jailtime in Russia (accepting money from a foreign intelligence agency could put him up on treason charges). Hence I would trust Passwork.me more with my private data as long as it remains in the hands of its founders.
I’d like to move from LastPass but we have both clients in LastPass (sharing password folders with us) and a team of over twenty-five both accustomed to LastPass and trained on it. The big downside with Passwork.me is that it does not do autofill and all the other tricks with which our team have been spoiled. In our case, we are a software development company and web agency with literally thousands of logins so autofill matters for us. For most companies, it wouldn’t.
I hope that helps.